911 Disruption
 Just last month, researchers explained how an attacker can knock the 911 service offline in an entire state by launching automated Distributed Denial of Service (DDoS) attacks using a botnet of just 6000 smartphones.
Just last month, researchers explained how an attacker can knock the 911 service offline in an entire state by launching automated Distributed Denial of Service (DDoS) attacks using a botnet of just 6000 smartphones.
But, doing so, in reality, could not only land the public in danger but the attacker as well.
An 18-year-old teen from Arizona was arrested this week following a severe disruption of 911 emergency systems due to one of his Apple iOS exploits.
Meetkumar Hiteshbhai Desai discovered an iOS vulnerability that could be exploited to manipulate devices, including trigger pop-ups, open email, and abuse phone features, according to a press release from the Cyber Crimes Unit of Maricopa County Sheriff's Office.
In order to prove the flaw, Desai allegedly created several exploits and posted a link to one of his JavaScript exploits on his Twitter account and other websites.
People accessing the exploit link from their iPhones and iPads were forced to call 911 non-stop, which flooded a 911 call center with more than 100 hang-up calls within a "matter of minutes" earlier this week.
After being notified of the disruption to the 911 service around the Phoenix, Arizona, area, investigators immediately launched an investigation and traced the Twitter link back to a web page registered to 'Meet Desai.'
The authorities identified Desai as the possible suspect behind the attack against the 911 service and took him into custody late Wednesday.
On his part, Desai claimed he just meant to upload a script that simply displayed pop-ups and caused iOS devices to reboot, but he mistakenly published a link to an exploit that caused iOS devices to dial 911 and hang up continually. According to authorities, Desai shared the critical iOS exploit on Twitter with over 12,000 followers, out of which over 1,849 clicked on that link.
Maricopa officers arrested Desai, took him to jail and booked him on three counts of felony computer tampering charges, on Monday, October 24.
Rule 41 Amendment Expands the Reach of Search Warrants (October 27, 2016)
An amendment to Rule 41 of the Federal Rules of Criminal Procedure will allow law enforcement agents to search electronic devices across the country with just one warrant. The amendment goes into effect on December 1, 2016. Civil liberties groups and other opponents are concerned that the amendment will give law enforcement an over-broad reach. Some legislators have proposed preventing it from taking effect. The US Justice Department has cited the distributed denial-of-service (DDoS) attacks fueled by poorly secured Internet of Things (IoT) devices to support its position that the amendment is necessary. ]
https://www.washingtonpost.com
Cyberattacks put new focus on search-warrant rule
Virus Cripples UK Hospital
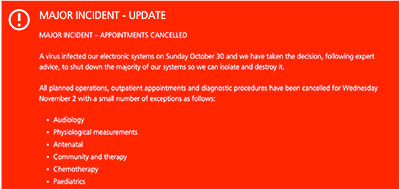
Citing a computer virus outbreak, a hospital system in the United Kingdom has canceled all planned operations and diverted major trauma cases to neighboring facilities. The incident came as U.K. leaders detailed a national cyber security strategy that promises billions in cybersecurity spending, new special police units to pursue organized online gangs, and the possibility of retaliation for major attacks.
In a “major incident” alert posted to its Web site, the National Health Service’s Lincolnshire and Google trust said it made the decision to cancel surgeries and divert trauma patients after a virus infected its electronic systems on Sunday, October 30.
“We have taken the decision, following expert advice, to shut down the majority of our systems so we can isolate and destroy it,” the NHS said, of the unspecified malware infection. “All planned operations, outpatient appointments and diagnostic procedures have been cancelled for Wednesday, Nov. 2 with a small number of exceptions.”
States seek cybersecurity help from DHS before elections
 Forty-six states are seeking cybersecurity help from the Department of Homeland Security before next week's elections. DHS can provide scanning services to the states, but finding flaws can take time -- and DHS said some states have found that systems have been scanned by hackers tied to Russia.
Forty-six states are seeking cybersecurity help from the Department of Homeland Security before next week's elections. DHS can provide scanning services to the states, but finding flaws can take time -- and DHS said some states have found that systems have been scanned by hackers tied to Russia.
Questions About Managed Services
The computer industry has changed over the past few years from one where Technicians charge you by the hour for the work they did, to one where you are charged by the month for a predefined list of services. This monthly “fee for service” arrangement has been dubbed Managed Services and an IT company doing business under this model is referred to as a MSP (Managed Service Provider).
This business model offers both the Client and the MSP a lot of benefits. Under an “All You Can Eat” program, all of your IT problems are covered by the monthly fee.
Back in the “old” days, when you discovered you had a computer problem you called a computer guy and hoped that he or she would answer the phone and then actually show up to fix the problem. Because you did not have a “partnership” with this person, there was no compelling reason for them to hurry to your office and work at your pace. Additionally, the computer guy was not on your network regularly performing maintenance because he was not getting paid to do that preventative stuff. This meant that he had no real knowledge of your software and hardware which translated into more down time and more billable time that you payed for while the diagnosis was taking place. In reality, the longer the repair took the more money the IT person made.
From a Client perspective Managed Services means you can budget for monthly IT expenses without any surprises. Depending on the program, you may still be responsible for Moves of equipment, Additions to the hardware, Changes to Internet service or Security Related subscriptions. Other high-end programs may include these items.
With a Managed Services contract, you have now incentivized the computer guy to respond quickly and become familiar with your network because the quicker he solves your problem, the more profitable he is.
From the MSP perspective, revenue becomes more predictable thereby allowing the MSP to invest in staffing and new technologies to better support your network. This model also allows the MSP to become intimately familiar with your network which means things can get fixed faster.
For more info, call me:
Talking is free…..
Hank Wagner
hank.wagner@computernetworksinc.com
www.computernetworksinc.com
757-333-3299 x232

Being “smart” isn’t just for phones and TVs anymore.
Soon, Microsoft’s Cortana will be able to see inside your fridge. With cutting-edge, fridge-safe technologies, Cortana can identify the foods you place there. After spending some time with your fridge’s contents, Cortana learns your food preferences. It can even offer up recipes or shopping lists to make your life easier. While other smart fridges have cameras that show users what’s inside without opening the door, the Cortana version actually helps you keep your fridge stocked. By the time this fridge hits the market, it will have captured thousands of photos of food packages from around the world. And that means you may soon have a smart new helper when it comes to shopping and fixing meals. –TechCrunch
Ditch the meeting, get more done.
The average manager spends 30%-50% of their time in meetings. And most feel 67% of meetings are an utter waste. So what can we do to stop killing time? Quit having meetings. Here are three ways to tell if a meeting is worthwhile. 1) Compare cost to benefit. Take the number of folks attending times their average pay rate. Multiply that by their time spent meeting. Is the desired outcome worth it? 2) Will this be a one-sided affair? A dead giveaway is the conference call when the boss puts everyone else on mute. 3) Is the meeting a guise for “communication”? Instead, send an e-mail, point to a website or suggest someone to consult with. Now you’re talking… -Entrepreneur
Want earbuds that last – and sound great?
Bragi’s new earbuds, named simply, “The Headphone” now have “bragging rights” on both battery life and sound quality. At six hours of battery life, these buds shred all competition. That includes Erato’s Apollo 7 and the Earin buds – both of which wimp out at three hours. Bragi’s Headphone also delivers a crystal-clear sound that beats most Bluetooth and WiFi earbuds. And they let sounds come through from whatever space you’re in. They also receive phone calls and respond to voice commands. Plus, all of this is 100% wireless. They even include a sleek-looking lanyard-style carrying case. All that being said, The Headphone is well worth a look if you’re looking for a great pair of earbuds. –DigitalTrends
Google’s Chromebook Pixel may have faded into a high-resolution sunset…
But the good news is, some great new challengers will soon take its place. The Dell Chromebook 13, for instance, sports a 1080p touch-screen display, aluminum chassis, glass trackpad and a (very fast) Intel Core i3 processor. Meanwhile, weighing in at just 2.9 pounds, the Toshiba Chromebook 2 delivers nearly the same performance as the Dell. Yet at a full two pounds less, you’ll appreciate its light weight. And the new kid on the block, the Acer Chromebook 14, offers a high-end feel and near top-of-the-line specs for just $300. Any of these challengers will fill the bill for you if you love the low price of a Chromebook, but want something a little more premium. -AndroidCentral.com
Phishing
Phishing (sounds like fishing) is a method of infecting a computer network with a virus or ransomware by sending an email to a user on the network. The emails are crafted by the criminals to trick your users into opening an attachment or clicking a link which starts the download process.
Never click on a link in an email or open an attachment unless you are certain of the source.





