New Mac Malware found Spying
 Many people believe that they are much less likely to be bothered by malware if they use a Mac computer, but is it really true? Unfortunately, No.
Many people believe that they are much less likely to be bothered by malware if they use a Mac computer, but is it really true? Unfortunately, No.
According to the McAfee Labs, malware attacks on Apple's Mac computers were up 744% in 2016, and its researchers have discovered nearly 460,000 Mac malware samples, which is still just a small part of overall Mac malware out in the wild.
Today, Malware Research team at CheckPoint have discovered a new piece of fully-undetectable Mac malware, which according to them, affects all versions of Mac OS X, has zero detections on VirusTotal and is "signed with a valid developer certificate (authenticated by Apple)."
Dubbed DOK, the malware is being distributed via a coordinated email phishing campaign and, according to the researchers, is the first major scale malware to target macOS users.
The malware has been designed to gain administrative privileges and install a new root certificate on the target system, which allows attackers to intercept and gain complete access to all victim communication, including SSL encrypted traffic.
Just almost three months ago, Malwarebytes researchers also discovered a rare piece of Mac-based espionage malware, dubbed Fruitfly, that was used to spy on biomedical research center computers and remained undetected for years.
Malware shuts down Virginia State Police email
The Virginia State Police network was hit with a malware attack April 26th which shut down the department's email services.
The attack also affected the department's ability to update the Virginia Sex Offender and Crimes Against Children Registry website and forced the department to suspend email services between 8 p.m. Wednesday and until noon Thursday, according to The Virginian-Pilot.
State police spokeswoman Corinne N. Geller told the publication police are working with the Virginia Information Technologies Agency and Northrup Grumman to identify, contain and eradicate the malware and that department field operations weren't affected by the attack.
“We recognize the vital role email plays in regards to communicating with State Police, and appreciate the public's patience and understanding as we diligently work to resolve this matter,” Virginia State Police Superintendent Colonel W. Steven Flaherty said in a press release obtained by CBS 6 TV. “While during this period we are required to communicate with the public through alternative means, our level of service should not otherwise be affected.”
Computer Networks of Roanoke, Inc.
Hank Wagner
hank.wagner @computernetworksinc.com
757-333-3299 x232

Webroot 'Mistakenly' Flags Windows As Malware And Facebook As Phishing Site
Popular antivirus service Webroot mistakenly flagged core Windows system files as malicious and even started temporarily removing some of the legit files, trashing user computers around the world.
The havoc caused after the company released a bad update on April 24, which was pulled after approximately 15 minutes. But that still hasn't stopped some PCs from receiving it, causing serious issues for not just individuals, but also companies and organizations relying on the software.
According to the reports by many customers on social media and Webroot's forum, hundreds and even thousands of systems were broken down after antivirus software flagged hundreds of benign files needed to run Windows and apps that run on top of the operating system.
Leaked NSA Hacking Tools Being Used to Hack Thousands of Vulnerable Windows PCs
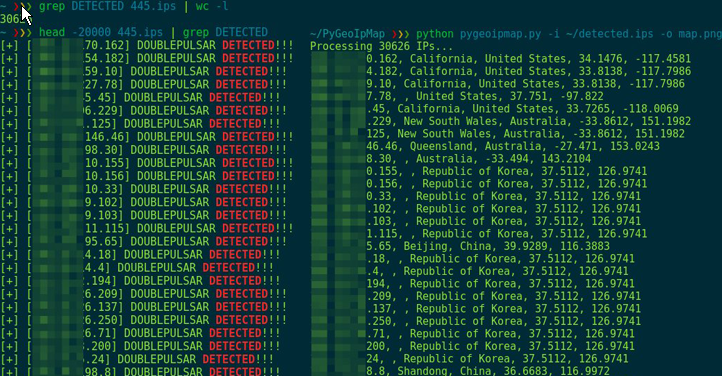
Script kiddies and online criminals around the world have reportedly started exploiting NSA hacking tools leaked last weekend to compromise hundreds of thousands of vulnerable Windows computers exposed on the Internet.
Last week, the mysterious hacking group known as Shadow Brokers leaked a set of Windows hacking tools targeting Windows XP, Windows Server 2003, Windows 7 and 8, and Windows 2012, allegedly belonged to the NSA's Equation Group.
Multiple security researchers have performed mass Internet scans over the past few days and found tens of thousands of Windows computers worldwide infected with DoublePulsar, a suspected NSA spying implant, as a result of a free tool released on GitHub for anyone to use.
Security researchers from Switzerland-based security firm Binary Edge performed an Internet scan and detected more than 107,000 Windows computers infected with DoublePulsar.
Meanwhile, Windows users who haven't applied MS17-010 by now are strongly advised to download and deploy the patches as soon as possible.
Ransomware Accounted For 72% Of Healthcare Malware Attacks In 2016
Of all the 2016 malware attacks on the healthcare industry, 72 percent were caused by ransomware, according to the Verizon 2017 Data Breach Investigations Report released Thursday.
The results may not surprise you, since the healthcare industry is one of the most targeted in the United States. Ransomware is one of its biggest threats, as hackers know how crucial data is to daily hospital operations. Therefore, many will pay to avoid disruption.
Ransomware attacks have doubled in frequency across all industries and are now the fifth most common specific malware variety, the Verizon report found. The healthcare industry was the second-most targeted industry at 15 percent of incidents, just behind the financial sector that had 24 percent of total incidents in 2016.
The report analyzed more than 2,000 breaches from 2016 and found that over 300 were related to espionage -- 62 of which stemmed from phishing emails. The healthcare industry was hit with 458 incidents, and 286 of these included improper data disclosure.
Ransomware first made its mark with the attack on Hollywood Presbyterian, which caused the organization to declare an internal emergency and pay the hackers $17,000 to regain control of its systems.
Provider Hit With $31,000 HIPAA Settlement Over Lack Of Business Associate Agreement
Center for Children’s Digestive Health shared protected health info with FileFax, but didn't have a BAA in place.
The failure of one Illinois specialist to procure a business associate's agreement has cost it more than $30,000 in a settlement with The U.S. Department of Health and Human Services.
The Center for Children’s Digestive Health, a small, for-profit pediatric subspecialty practice that operates seven clinic locations in the Chicago area, had contracted in 2003 with FileFax, a Northbrook, Illinois-based firm that stores medical records.
Despite the fact that the files contain protected health information, an investigation from HHS' Office for Civil Rights discovered that neither party could show a signed business associate agreement prior to Oct. 12, 2015.
In May of 2015, the Illinois Attorney General brought suit against FileFax for improper handling of PHI, charging that its employees had tossed the paper medical records of thousands of patients into an unlocked dumpster.
That summer, during a compliance review of Center for Children’s Digestive Health, OCR found that CCDH had "failed to obtain satisfactory assurances from Filefax, in the form of a written business associate agreement, that Filefax would appropriately safeguard the PHI" that was in the company's possession.
Despite not having a BAA in place, the provider shared the records of at least 10,728 people, according to OCR.
To settle the charge, the provider will pay HHS $31,000 and enter into a corrective action plan to develop policies and procedures in compliance with federal privacy and security standards, educate its staff about proper handling of PHI and provide HHS a list of all of its business associates, with a signed BAA for each.
Crafty Phishing Technique Can Trick Even Tech-Savvy Gmail Users
Gmail users in recent months have been targeted by a sophisticated series of phishing attacks that use emails from a known contact whose account has been compromised. The emails contain an image of an attachment that appears to be legitimate, according to Wordfence.
The sophisticated attack displays "accounts.gmail.com" in the browser's location bar and leads users to what appears to be a legitimate Google sign-in page where they are prompted to supply their credentials, which then become compromised.
The technique works so well that many experienced technical users have fallen prey to the scam, noted Mark Maunder, CEO of Wordfence. Many have shared warnings on Facebook to alert family and friends, given that the technique has exploited otherwise trusted contacts so successfully.