Cloud/Schmoud

Being able to store one’s data at a location other than where the data is created is a good philosophy. This is what Cloud based systems do.
What we have to be concerned about is the Cloud companies, and the people who work at those Cloud companies, to whom we have entrusted that data and whether there are regulatory compliance issues, such as HIPAA, that we have to be concerned about before putting our data there.
If you are a Sales organization, and don’t want to purchase & maintain servers, then Cloud based Salesforce.com may be a good fit for your business.
If you have representatives of your business scattered all over the country or world, putting your data in a Cloud environment may be beneficial to you.
If you’re a Physician’s office maintaining my medical record, I probably won’t do business with you if you have my medical records in the Cloud.
Because of regulatory compliance with HIPAA, we are not advocates of Cloud based Practice Management (PM) & Electronic Health Record (EHR) systems, unless those systems are housed & maintained solely by the PM or EHR Vendor in a Private Cloud.
The Omnibus 2013 changes to HIPAA dictate that most everyone in possession of ePHI (electronic Protected Health Information) becomes a Business Associate (BA) of the Physician’s office & has to comply with all of the regulations that the CE (Covered Entity/Physician’s Office) has to. That means that your BA’s must complete a Security Risk Analysis, train all staff in HIPAA, write & implement Policies & Procedures, execute a Business Associate Agreement (BAA) with the CE/Physician’s Office & ensure that all of it is kept up to date.
Amazon, Google and other Cloud Vendors are unwilling to sign BAA’s because they are not going to comply with the aforementioned Federal law. Additionally, any IT Vendor a medical office does business with is also required to comply with all those same rules as the CE/Physician’s office.
If all this confuses you, you are not alone. If worrying about HIPAA keeps you up at night, call us and we can steer you in the right direction!

From Krebs on Security:
http://krebsonsecurity.com/
The U.S. Internal Revenue Service (IRS) today sharply revised previous estimates on the number of citizens that had their tax data stolen since 2014 thanks to a security weakness in the IRS’s own Web site. According to the IRS, at least 724,000 citizens had their personal and tax data stolen after crooks figured out how to abuse a (now defunct) IRS Web site feature called “Get Transcript” to steal victim’s prior tax data.
Computer maker Dell is asking for help in an ongoing probe into the source of customer information that appears to have somehow landed in the laps of fraudsters posing as Dell computer support technicians. KrebsOnSecurity readers continue to report being called by scammers posing as Dell support personnel who offer “proof” that they’re with Dell by rattling off the unique Dell “service tag” code printed on each Dell customer’s PC or laptop, as well as information from any previous (legitimate) service issues the customer may have had with Dell.
Scam artists have been using hacked accounts from retailer Kohls.com to order high-priced, bulky merchandise that is then shipped to the victim’s home. While the crooks don’t get the stolen merchandise, the unauthorized purchases rack up valuable credits called “Kohl’s cash” that the thieves quickly redeem at Kohl’s locations for items that can be resold for cash or returned for gift cards.
Let’s Go Phishing!
So, it’s a pleasant, peaceful start to the day. You get logged in and click on a network shared drive and you cannot open any of the files. What the heck? Then one of your staff comes to you and says, “I have this funny message on my screen”. You go look at their PC and see something similar to this:
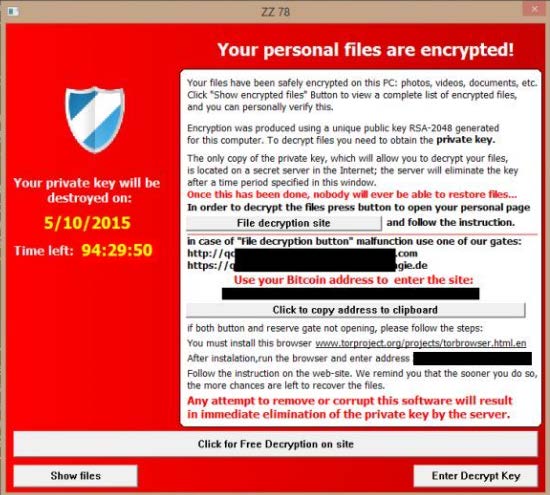
You are officially at an “Aw,$&^%” moment in your life.
So, what happened to get us to this point? Your staff went phishing and your IT support company did not catch it. You pronounce it like fishing, but, the crooks are doing the phishing and not you.
Your staff member clicked on an email link or attachment in an email, probably from someone they did not know, and downloaded ransomware to your network.
Ransomware encrypts all the files it can find on all drives, INCLUDING NETWORK DRIVES (that means the server). When it has done its dirty deeds, you get a message similar to the one shown. There is a demand for money, i.e., a ransom demand.
If you pay, some of the criminals will send you a key code to decrypt your files. And, some just laugh and keep your money, leaving you with encrypted files that cannot be unlocked.
In that case, the only way to recover your business is to have a good, tested backup as part of a comprehensive Disaster Recovery Plan with Data Center backups, use those backups to restore from, and then re-key the missing data between the time the malware struck and your latest backup.
The takeaways:
- train your staff not to click on anything they do not know or are not expecting
- backup hourly
- backup offsite daily
- test the backups regularly
Staff is always the weakest link in the Security process. Develop an office culture of security and train the staff what not to do.

5 Ways To Prevent Facebook Identity Theft
1. Don't post your birth date, or at least don't post the year you were born. It might seem like a tactic for people who just want to cling to their 20s for as long as possible, but it actually has a practical use: Your birth date, year included, is a key piece of information to steal your identity.
2. Think twice when you want to purchase Facebook services that require your credit card information. It's best to avoid putting that data on the site.
3. Have boundaries. Avoid revealing where a photo was taken and stop geotagging photos that show exact locations. Be cautious about posting pics that reveal your address or show where you keep valuables in your home.
4. The more you publicly reveal where you are and what you are doing, identity thieves will surely take notice. Delete photos and posts on your timeline that show personally identifiable information.
5. Your name, profile picture, and cover photo are all always "public" and that cannot be changed. From this public information, thieves can create identical Facebook profiles aimed at infecting users' devices with spyware that can steal precious data. Use reputable internet security software on your device to weed out dangerous threats for effective identity theft protection. Also, be extra cautious of downloading free anti-spyware packages, which could be malware in disguise!
Last year the Federal Trade Commission reached a settlement with Facebook to make sure the site took certain privacy steps; that's good news for users concerned about privacy, but you should be your own advocate to prevent identity theft.
For more than one billion people and counting, Facebook has been a venue to connect with old friends, keep in touch over long distances and promote new business ventures. If you use it wisely and with a bit of precaution, Facebook can be a great tool. If not, the bad guys out there may just ruin the fun.
3 Ways To Protect Yourself
Spam Email Prevention
In addition to protection against malware, you also should be alert for spam and phishing emails that attempt to steal your identity. Spam emails pose a threat to consumers because they're commonly laden with malware or, in many cases, they lead victims to malicious websites designed to scam individuals. Typical spam messages include off-shore pharmaceutical ads, pump-and-dump stock schemes and general unsolicited advertising. These emails lead the unwary to fake sites, which then usually include "notifications" about their accounts being at risk or needing updates. A simple click on these notifications will compromise your computer's security.
Phishing Prevention
Phishing is another common type of cybercrime. Victims receive an email — usually appearing to be from a bank or a financial institution — saying the victim's account is in jeopardy and that he or she must "confirm" some details to save the account. The emails contain links that appear to go to the proper financial site, however they actually go to the criminals' servers, where they steal your account credentials. As a rule of thumb, it is best to never click links in emails to get to a website. Instead, if you get a notice from a company, you can open your browser and type the website name directly into the address bar. If it turns out your account is OK, you can then call or email the company to report the phishing message.
Cybercrime Protection
To protect yourself from these threats along with malware, it is crucial to have a comprehensive Internet security suite installed on your system. Key features of Internet security suites include virus protection, spam filters, parental controls and many other safeguards to protect against all types of cybercrime. One of the most important features of such suites is cloud based security protection which ensures that when browsing the web, if you visit a malicious website, it will be blocked before you become a victim. Additionally safe banking software included with many suites adds an additional layer of protection by ensuring that when you visit a banking website, it actually is the legitimate entity.
If you need help with your office computers, have doubts about the security of your network, or questions about your Backup and Disaster Recovery solution, give us a call. We are the IT Support and IT Managed Service company for several Doctor’s Offices in our area.
It doesn’t cost a dime to talk. You don’t have to buy anything from us. Our job is education.
The Lighter Side: Signs
Sign over a Gynecologist Office:
Dr. Jones, at your cervix.
In a Podiatrist's office:
Time wounds all heels.
At an Optometrist's Office:
If you don't see what you're looking for,
You've come to the right place.
On a Plumber's truck:
We repair what your husband fixed.
At a Tire Shop in Milwaukee:
Invite us to your next blowout.
On an Electrician's truck:
Let us remove your shorts.
In a Non-smoking Area:
If we see smoke, we will assume you are on fire and will take appropriate action.
Outside a Muffler Shop:
No appointment necessary. We hear you coming.
In a Veterinarian's waiting room:
Be back in 5 minutes. Sit! Stay!
At the Electric Company:
We would be delighted if you send in your payment on time.
However, if you don't, YOU will be de-lighted.
In the front yard of a Funeral Home:
Drive carefully. We'll wait.
In a Chicago Radiator Shop:
Best place in town to take a leak.
And the best one for last.
Sign on the back of another Septic Tank Truck:
Caution
"This Truck is full of Political Promises."




