
TDO Strikes Again
There is a hacker on the Internet who called himself/herself The Dark Overlord (TDO). It seems that this person specializes in breaking into medical office networks and then extorting money from the medical practice to keep quiet about the HIPAA data breach.
His latest target is the Austin Manual Therapy Association, a physical therapy operation, located in Austin, TX.
TDO has provided www.databreaches.net with a sample of the hacked Protected Health Information that included individual patient information and insurance authorization information.
This is the 8th extortion attempt by TDO in September. In May, TDO exposed the data of 180,000 patients when his extortion attempt on Aesthetic Dentistry and OC Gastrocare failed. The hacker leaked celebrity patient data from California-based Dougherty Laser Vision in June. And just last month, TDO began attempting to extort Massachusetts-based SMART Physical Therapy. And there are others.
These extortion attempts are increasing in every sector and the “healthcare sector and education sector are prime targets for extortionists due to the sensitivity of the data and the lack of security when compared to other sectors” according to www.databreaches.net.
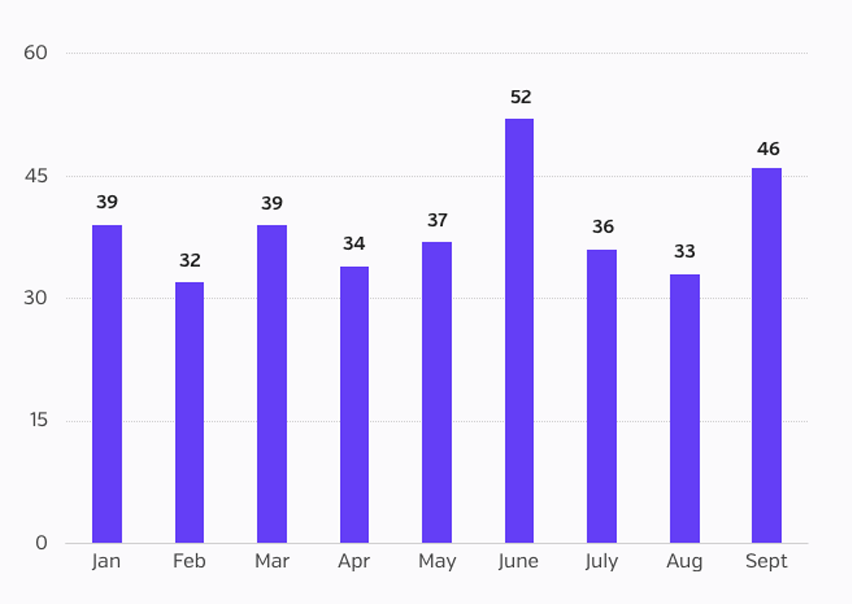
2017 Data Breaches Involving ePHI
(source www.post-healthcare.com)
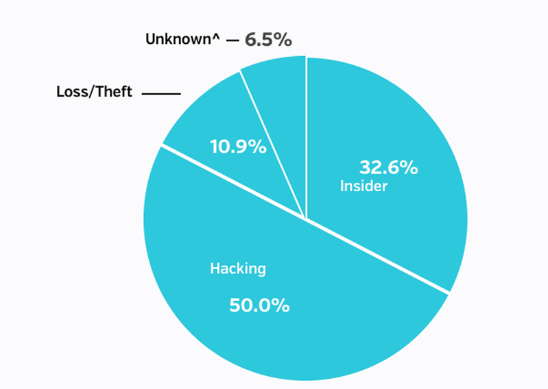
Insider Wrongdoing Almost As Bad As Hackers
A New Kind of Krack
http://www.kb.cert.org/vuls/id/228519
The Department of Homeland Security issued a warning on October 16, 2017 about a flaw that has been discovered in the WPA2 WiFi Security protocol that we all use to protect out wireless networks.
WPA2 is used to secure and protect communications between routers, mobile devices and IoT devices. But a flaw in the system’s four-way handshake -- which permits devices with a pre-shared password to join a network, would allow hackers to hijack connections, decrypt traffic and view communications sent from WPA-2 enabled devices.
US-CERT was made aware of the flaw a few months ago and began notifying vendors of the flaw ahead of today’s alert to give them time to prepare patches. Currently, there are no reports of a successful hack of KRACK in the wild.
The takeaway is for you to insure that you have the latest firmware installed on all of your wireless (WiFi) devices.
Data On 150,000 Patients Exposed In Another Misconfigured Amazon Web Services Server
Kromtech Security researchers have discovered yet another unsecured Amazon S3 bucket. This time, the cloud server in question was linked to HIPAA-covered entity, Patient Home Monitoring, a vendor that provides U.S. patients with disease management services and in-home monitoring.
The misconfigured server contained the lab results and other patient files of about 150,000 patients. The files were stored on a publicly accessible bucket that was left unprotected by a password, according to researchers.
In total, the breach contained 47.5 GBs of data comprised of about 316,000 PDF files, which contained patient names, addresses, phone numbers, diagnoses and test results. The files also contained physician names, case management notes and other patient information.
“Anyone with an internet connection could access these confidential records,” said Alex Kernishniuk, vice president of Strategic Alliances for Kromtech, in a statement.
128,000 Patient Record Breach
A ransomware attack on Fayetteville-based Arkansas Oral Facial Surgery Center has potentially breached the data of 128,000 of its patients.
An investigation found the cyberattack occurred between July 25 and 26, and while quickly detected, the virus encrypted x-ray images, files and documents. Fortunately, the patient database was not encrypted.
However, hackers managed to infect the data of a small number of patients who visited the provider within three weeks prior to the incident.
The potentially accessed files contained names, Social Security numbers, addresses, dates of birth, insurance information, diagnoses, treatments and other medical data. The virus also shut the organization out of medical images, details of patient visits and files.
It is important to understand that HHS and OCR have taken the position that an unauthorized access of the computer network (such as ransomware) is considered a breach of ALL of your Patient Records absent any evidence to the contrary.
Update Now
When a software or hardware Vendor releases a patch or bug fix, the time to apply that fix is now. That means as soon as it is released.
There is just too much risk these days in waiting a month or two (or forever) to apply bug fixes and patches.
Do not become complacent about the security of your network, your website or your mobile devices. If a patch is out, apply it now, deal with any consequences and move on. You are vulnerable until you do.
Hackers Agree: Phishing Is The Best Way To Steal Data
 At the 2017 Black Hat national cybersecurity conference, Cybersecurity firm Bitglass surveyed 129 attendees on the best way to access a business electronically.
At the 2017 Black Hat national cybersecurity conference, Cybersecurity firm Bitglass surveyed 129 attendees on the best way to access a business electronically.
Fifty-nine percent of respondents identified phishing as the best data exfiltration strategy, as human error and ignorance will always be exploitable.
The report found that the top 5 security blind spots are:
- unmanaged devices (61 percent)
- systems/applications/programs not up to date (55 percent)
- mobile devices (36 percent)
- data at rest in the cloud (26 percent)
- and traditional on-premises security (20 percent)
What does this mean to you?
Train, train, train and then train some more. You employees are your weakest link in this puzzle.
Just recently, a long-time staffer at one of our client’s offices was on the Internet and got a pop-up window telling her that the machine she was using was infected and to call an 800 number to get the machine fixed.
Instead of reporting this to us or to her management, she called the 800 number and then allowed someone on the other end of the phone to take over her work computer. Eventually, when the crooks started asking for credit card information, she reported the problem to management who then involved us. But, the horse was out of the barn and across the pasture.
The client now has a reportable data breach and is in the process of doing an Incident Investigation to determine if this was a breach of all of their Patient records.
Your staff is the weakest link in your security. Train them to think before they click!
Monitor Your Business Associates!
https://www.hipaajournal.com/monitor-business-associates-hipaa-compliance/
Should covered entities monitor business associates for HIPAA compliance or is it sufficient just obtain a signed, HIPAA-compliant business associate agreement?
If a business associate provides reasonable assurances to a covered entity that HIPAA Rules are being followed, and errors are made by the BA that result in the exposure, theft, or accidental disclosure of PHI, the covered entity will not be liable for the BA’s HIPAA violations – provided the covered entity has entered into a business associate agreement with its business associate.
It is the responsibility of the business associate to ensure compliance with HIPAA Rules. The failure of a business associate to comply with HIPAA Rules can result in financial penalties for HIPAA violations for the business associate, not the covered entity.
A covered entity should ‘obtain satisfactory assurances’ that HIPAA Rules will be followed prior to disclosing PHI. While covered entities are not required by HIPAA to monitor business associates for HIPAA compliance, they should obtain proof that their business associate has performed an organization-wide risk analysis, has developed a risk management plan, and is reducing risks to an acceptable and appropriate level.
If information is provided to a covered entity which suggests noncompliance, a covered entity must act on that information. The failure of a covered entity to take appropriate action to resolve a known breach of HIPAA Rules by a business associate would be a violation of HIPAA Rules. If the business associate cannot resolve that breach, it is the responsibility of the covered entity to terminate the business associate agreement. 45 CFR § 164.504(e)
A covered entity will be in violation of HIPAA Rules if it “knew of a pattern of activity or practice of the business associate that constituted a material breach or violation of the business associate’s obligation under the contract or other arrangement, unless the covered entity took reasonable steps to cure the breach or end the violation.” If termination of the BAA is not feasible, the problem must be reported to the Department of Health and Human Services’ Office for Civil Rights (OCR).
Even though a covered entity is not liable for business associate HIPAA violations, any business associate breach is likely to reflect badly on the covered entity and is likely to cause harm to its patients or members. It is therefore in the interests of both parties to ensure HIPAA Rules are being followed. It may help to provide business associates with a HIPAA compliance checklist to assist them with their compliance efforts, and access to other resources to help them prevent breaches and mitigate risk.
This newsletter is provided as a professional courtesy to you and your staff. Feel free to distribute as you see fit or to use in your training program.
Hank Wagner
Owner
757-333-3299 x232
hank.wagner@computernetworksinc.com




