Ponemon: 48% of Healthcare Organizations Suffered a PHI Breach in the Past Year
A study recently published by the Ponemon Institute has revealed that almost half of healthcare organizations (48%) have experienced a data breach in the past 12 months that has resulted in the loss or exposure of the protected health information of patients.
The survey, conducted on behalf of software security firm ESET, asked 535 IT security professionals questions about cyberattacks on their organizations, the consequences of those data breaches, and cybersecurity concerns.
Cyberattacks on healthcare organizations are now taking place at a rate of one every month.
Hackers were able to evade intrusion prevention systems (IPS) at 49% of organization surveyed, while 37% of respondents said cyberattackers had evaded detection by their antivirus protections and other traditional security measures.
Most commonly, hackers took advantage of unpatched software vulnerabilities. 78% of respondents said attacks occurred as a result of unpatched software where a patch had been available for at least 3 months. 70% said incidents had occurred as a result of unpatched software where a patch had been available for less than three months.
Three quarters of respondents said they had suffered security incidents as a result of web-borne malware attacks, while spear phishing attacks were also common, with 69% of respondents saying they had experienced such an attack.
Over the past year, employee negligence has resulted in numerous data breaches; however, the survey indicated that technology was a bigger problem. 52% of respondents said they believe the security vulnerabilities that exist in legacy systems, IoT (Internet of Things), and cloud and mobile applications were the biggest problem, while 46% were concerned about employee negligence.
Larry Ponemon, founder and chairman of the Ponemon Institute, said “Based on our field research, healthcare organizations are struggling to deal with a variety of threats, but they are pessimistic about their ability to mitigate risks, vulnerabilities and attacks,” he also said that as a result of the significant number of attacks suffered recently, “there is more pressure than ever for healthcare organizations to refine their cybersecurity strategies.”
All of these are good reasons for hiring a great IT company that stays on top of all things on your computer network!
WARNING-YOUR PHONE IS AT RISK
Hackers have discovered a new way to install malicious apps onto your iPhone without your interaction.
Researchers at Palo Alto Networks have uncovered a new strain of malware that can infect Non-Jailbroken (factory-configured) iPhones and iPads without the owner's knowledge or interaction, leaving hundreds of millions of Apple iOS devices at risk.
Dubbed AceDeceiver, the iPhone malware installs itself on iOS devices without enterprise certificates and exploits designing flaws in Apple's digital rights management (DRM) protection mechanism called FairPlay.
What's more concerning about this malware is that unlike most iOS malware, AceDeceiver works on factory-configured (non-jailbroken) iOS devices as well.
FairPlay is an Apple's software program that prevents people from stealing purchased apps from its official App Store.
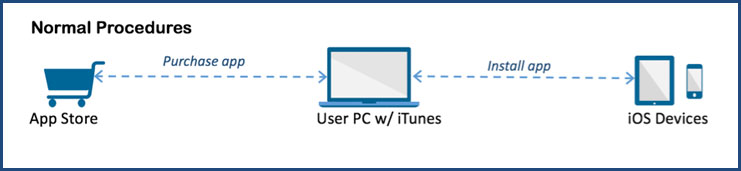
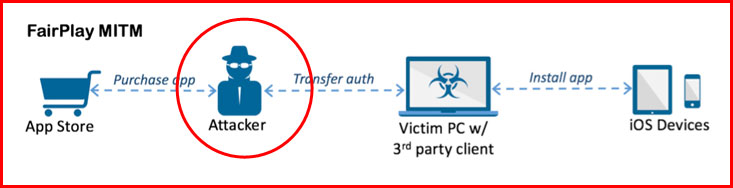
However, with the help of AceDeceiver's "FairPlay Man-in-the-Middle (MITM) technique," hackers can install malicious apps on your iPhone even without your knowledge, simultaneously bypassing Apple's other security defenses.
"In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code," Claud Xiao from Palo Alto Networks explains in a blog post. "They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by the victim.
MISSED BOAT
So, if you have yet to:
- Take protection of PHI seriously
- Conduct a Security Risk Analysis
- Update an existing Security Risk Analysis
- Develop a Culture of Compliance
- Look at HIPAA as a journey
- Document your compliance
You are missing the boat. The Federal Government is about to “break bad” on the medical offices that are failing or refusing to take the HIPAA process seriously.
You must develop a new way of thinking. Compliance with HIPAA is now a part of everyday life and it is not just about having a Notice of Privacy Practices for your Patients to sign every now and again.
You must have Physical, Technical and Administrative safeguards in place, you must have documentation of how you have met these safeguards and you must have an ongoing review process.
Ignoring these HIPAA rules is akin to ignoring the Internal Revenue Services. You can do it, but, when you get caught it is not going to be pretty and it is going to be very expensive.
Do not put your Physician/Owner’s business in jeopardy. Talk to us about a Security Risk Analysis today and what you need to do to get and remain compliant.
HHS Announces 2016 Covered Entity Audits

Deven McGraw, HHS, Deputy Director for Health Information Privacy
HHS has announced that they intend to conduct more than 200 HIPAA Compliance “desk” audits of Covered Entities before the end of 2016. They are using these audits to determine what additional steps they need to take before large scale, nationwide audits begin.
Once they pick you for an audit, HHS/OCR intends to gather copies your Business Associate Agreements and will proceed to audit your Business Associates. (You do have a BAA, dated after September 2013 containing all of the Omnibus rule changes, with all your Vendors who are exposed to Protected Health Information, don’t you?)
Ms. McGraw stated in an interview at the HIMSS conference earlier this month that HHS/OCR had “launched” the program and was in the process of putting together “pools” of CEs and BAs from which to choose auditees.
Wake up and smell the coffee folks…
- get your Security Risk Analysis done
- get it documented
- create your Policies and Procedures
- update your Business Associate Agreements
- fix the problems that you found
- repeat the process annually
No one is immune. Your Practice is NOT too small.
There is PHI in places that you do not believe have PHI, there are staff using work-arounds that expose PHI to others, there are employees who do not understand and sometimes do not care, you have PHI on your Smartphone, at your answering service, with the transcription service…
PHI is everywhere. Find it. Protect it.
Computer Networks of Roanoke, Inc.
Hank Wagner, Owner
hank.wagner@computernetworksinc.com
757-333-3299 x232
It doesn’t cost anything to talk.
So, if what I am saying is falling on deaf ears or does not resonate with you, consider this headline from March 16, 2016:
$1.55 Million Settlement Underscores the Importance of Executing HIPAA Business Associate Agreements
North Memorial Health Care has agreed to settle charges that it potentially violated the Health Insurance Portability and Accountability Act of 1996 (HIPAA) Privacy and Security Rules by failing to implement a business associate agreement with a major contractor and failing to institute an organization-wide risk analysis to address risks and vulnerabilities to its patient information.
North Memorial is a comprehensive, not-for-profit health care system in Minnesota that serves the Twin Cities and surrounding communities. The settlement includes a monetary payment of $1,550,000 and a robust corrective action plan.
“Two major cornerstones of the HIPAA Rules were overlooked by this entity,” said Jocelyn Samuels, Director of the U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR). “Organizations must have in place compliant business associate agreements as well as an accurate and thorough risk analysis that addresses their enterprise-wide IT infrastructure.”
OCR initiated its investigation of North Memorial following receipt of a breach report on September 27, 2011, which indicated that an unencrypted, password-protected laptop was stolen from a business associate’s workforce member’s locked vehicle, impacting the electronic protected health information (ePHI) of 9,497 individuals.
In addition to the $1,550,000 payment, North Memorial is required to develop an organization-wide risk analysis and risk management plan, as required under the Security Rule. North Memorial will also train appropriate workforce members on all policies and procedures newly developed or revised pursuant to this corrective action plan.
Full Press Release:
From this point forward, you are living on borrowed time if you have not completed your Security Risk Analysis and taken care of the things that go with that such as remediation of the problems found, creating Policies and Procedures and getting the staff trained in HIPAA.
If your Physician can:
- afford to write a check to the government for a million, five hundred thousand bucks
- then have the Practice still be required do the things you were supposed to be doing in the first place (which would have prevented the writing of the check)
- and, you can keep your job through all of it, then more power to you. I’ll sit down and shut up.
For those of you not in that camp, we see our job as the educators of folks who are not up to speed on these things and who do not keep their finger on the pulse of things happening at HHS and OCR. We want you to know what you do not know.
We have made a career out of being computer specialists with a focus on HIPAA compliance and it is our desire to share that knowledge through these monthly newsletters and publications.
Don’t let this be your Physician.

Computer Networks of Roanoke, Inc.
Hank Wagner, Owner
hank.wagner@computernetworksinc.com
757-333-3299 x232
It doesn’t cost anything to talk.




