Presence Health settles HIPAA breach for $475,000
January 10, 2017
Latest HIPAA enforcement action; updated guidance and FAQ; Privacy Policy Snapshot Challenge
 OCR has announced the first HIPAA settlement based on the untimely reporting of a breach of unsecured protected health information (PHI). Presence Health has agreed to settle potential violations of the HIPAA Breach Notification Rule by paying $475,000 and agreeing to implement a corrective action plan. Presence Health is one of the largest health care networks serving Illinois and consists of approximately 150 locations, including 11 hospitals and 27 long-term care and senior living facilities. Presence also has multiple physicians’ offices and health care centers in its system and offers home care, hospice care, and behavioral health services. With this settlement amount, OCR balanced the need to emphasize the importance of timely breach reporting with the desire not to disincentive breach reporting altogether.
OCR has announced the first HIPAA settlement based on the untimely reporting of a breach of unsecured protected health information (PHI). Presence Health has agreed to settle potential violations of the HIPAA Breach Notification Rule by paying $475,000 and agreeing to implement a corrective action plan. Presence Health is one of the largest health care networks serving Illinois and consists of approximately 150 locations, including 11 hospitals and 27 long-term care and senior living facilities. Presence also has multiple physicians’ offices and health care centers in its system and offers home care, hospice care, and behavioral health services. With this settlement amount, OCR balanced the need to emphasize the importance of timely breach reporting with the desire not to disincentive breach reporting altogether.
The Press Release, Resolution Agreement, and Corrective Action Plan may be found on the OCR website at http://www.hhs.gov/hipaa/for-professionals/compliance-enforcement/agreements/presence
OCR’s guidance on breach notification may be found at http://www.hhs.gov/hipaa/for-professionals/breach-notification/index.html
OCR has issued a new FAQ clarifying the HIPAA Privacy Rule
(45 CFR 164.510(b)) permits disclosures to loved ones regardless of whether they are recognized as relatives under applicable law. The FAQ, while applicable in a variety of circumstances, was developed in large part to address confusion following the 2016 Orlando nightclub shooting about whether and when hospitals may share protected health information with patients’ loved ones. In particular, the FAQ makes clear that the potential recipients of information under the relevant permissive disclosure provisions of 45 CFR 164.510(b) are not limited by the sex or gender identity of the person.
In tandem, OCR is updating its existing guidance on several provisions within the HIPAA Privacy Rule that recognize the integral role that a spouse often plays in a patient’s health and health care. Consistent with the Supreme Court decision in Obergefell v. Hodges, OCR is issuing updated guidance that makes clear that the terms marriage, spouse, and family member include, respectively, all lawful marriages (whether same-sex or opposite-sex), lawfully married spouses and the dependents of all lawful marriages, and clarifies certain rights of individuals under the Privacy Rule.
OCR’s updated guidance and FAQ may be found at: https://www.hhs.gov/hipaa/for-professionals/special-topics/same-sex-marriage/index.html and the FAQ is also available at https://www.hhs.gov/hipaa/for-professionals/faq/2086/does-hipaa-privacy-rule-permit-doctor-discuss-patient-s-health-status.html

5 Big Things from 2016
- Human Error
- Ransomware
- Backups/Disaster Recovery
- Risk Management
- Outdated Technology
The “loose screw” (your employee) behind the keyboard remains the biggest threat to your network security. Awareness training is required by HIPAA and should be conducted regularly enough to make an impact on those staff who will click on anything in an email they receive.
Ransomware is a big money-maker for the cyber-crooks and don’t expect that to change. The prices for stolen medical records are dropping so the crooks need to up their volume of theft to keep their incomes the same. You have to take any and all reasonable steps to protect the ePHI you have in your possession.
Backup and Disaster Recovery technology has left tape drives in the dust. We now have the ability to back up your servers and all the data every hour, turn that data into a Virtual Machine (VM) that can be used if a physical server goes down. Moving backups offsite is rapidly becoming the norm for most IT Service Providers.
Knowing what is at risk allows one to minimize those risks. A good, solid, well-done, onsite Security Risk Analysis is the first step in identifying the risks in your business so that you can start taking the steps to eliminate them.
You have to keep up on the technology. Especially when it comes to UTM (Unified Threat Management) Security firewalls. You have to put some strong defenses at the edge of your network where the Internet comes in. That is done with a UTM firewall running all of the Vendor’s Security Subscriptions enables and up to date.
More From OCR
It is important for us to note that the Federal Government relies on its arm called NIST (National Institute of Standards and Technology) to provide rules by which the Government runs. Therefore you will see a lot of the OCR info refer back to NIST. OCR expects healthcare to closely follow the NIST rules when it comes to HIPAA Compliance. This is an important fact to remember when reviewing your compliance plan.
January 13th’s guidance email from the Office for Civil Rights (OCR) covers Audit Controls. As part of your HIPAA compliance, you are required to maintain logs for a period of 6 years.
NIST says that:
audit logs are records of events based on applications, users, and systems, and audit trails involve audit logs of applications, users, and systems.
Audit trails’ main purpose is to maintain a record of system activity by application processes and by user activity within systems and applications.
Your EHR (Electronic Health Record) software has audit logging built into the software by the Vendor.
- You need to be reviewing the activity in these logs to insure that your staff is using the EHR properly and are not improperly accessing records that they should not be.
- Where a lot of folks fall down on the job is auditing ePHI (electronic Protected Health Information) that is located outside of the EHR, such as in shared folders on your network. If you are keeping old records, insurance appeals letters, patient referral forms, scanned images or any other ePHI on a Server or PC outside of your EHR software (everyone does), then you must have a way of auditing access to that information at a level in accordance with NIST standards.
- You also need to be logging network intrusion activity at the firewall and on the Microsoft Windows machines. Your EHR software does not do that either.
This is going to involve buying some 3rd party software from your IT Vendor in order to be in compliance.
NIST defines audit trails:
Application audit trails – Normally monitor and log user activities in the application. This includes the application data files opened and closed, and the creating, reading, editing, and deleting of application records associated with ePHI.
System-level audit trails – Usually capture successful or unsuccessful log-on attempts, log-on ID/username, date and time of each log-on/off attempt, devices used to log-on, and the application the user successfully or unsuccessfully accessed.
User audit trails – Normally monitor and log user activity in a ePHI system or application by recording events initiated by the user, such as all commands directly initiated by the user, log-on attempts with identification and authentication, and access to ePHI files and resources.
Software that does all of this is sometimes called SIEM or Security Incident and Event Management software. We are evaluating several SIEM Vendors so that we can offer a higher level of auditing to better help you become and remain HIPAA compliant. There is just too much data generated to look at all of it, so reporting is based on outliers. A daily/weekly scheduled report of the exceptions, retained for 6 years, is a requirement for HIPAA compliance.
Office 365 Email
If you have been using Yahoo email (or any email hosted by an Internet Service Provider) and you are sending and receiving ePHI, you are most certainly committing a data breach each time you send one of those emails. Since Yahoo! lost one Billion records (yes, 1 Billion) and the associated password reset questions, you may want to consider Microsoft Office 365. This is Microsoft’s cloud offering for business grade email that meets the standards required for HIPAA compliance.
HIPAA Enforcement 2017 Predictions
 Attorney David Holtzman Sizes Up Outlook for HHS Activities
Attorney David Holtzman Sizes Up Outlook for HHS Activities
The transition to a new presidential administration makes forecasting for 2017 and beyond particularly challenging. That's because President-elect Trump's positions on health information privacy and security are not well known.
Tom Price, Trump's pick to be the next HHS secretary, is a physician and a member of the House of Representatives who has generally supported the development of health information technologies. But he's a frequent critic of what he describes as burdensome regulations on healthcare providers. For example, he sponsored legislation to scale back the reporting requirements for providers participating in the HITECH Act's "meaningful use" electronic health record incentive payment program.
Jocelyn Samuels will step down as head of OCR before Trump takes his oath of office on Jan. 20. It's unlikely that the Trump administration will appoint a new OCR director anytime soon. While the job is important, it is not politically sensitive. Poised to take the reins are career senior staff who have been with the agency for many years. Watch for Principal Deputy Robinsue Frohboese or Deputy Director for Operations Steve Novy to lead on an acting basis until a permanent director is named.
Look for 2017 to be a year when OCR continues to exercise its HIPAA enforcement muscle - just not at the record pace seen in 2016.
OCR has been on a tear, settling 11 cases in 2016 with resolution agreements and corrective action plans.
Since the middle of 2015, OCR has collected more than $27 million in penalties from covered entities and business associates. And behind the scenes, the agency has closed hundreds of other compliance reviews that forced organizations to take actions to update their compliance policies or safeguards for protecting health information.
The common denominator for many of the cases in which there was a settlement was that the covered entity or business associate suffered one or more breaches affecting more than 500 individuals sometime between 2011 and 2013. The enforcement actions came about when investigations into the root cause of the breach found systemic, often profound, failures of organizational programs to safeguard protected health information. And most often cited was failure to perform an information security risk assessment or to have a risk management plan to address gaps in the safeguards for information systems, both required actions under the HIPAA Security Rule.
So, the takeaway is keep on plugging away at compliance. The rules are not going to change and if you get caught up in an audit, you and your pocketbook are going to wish you had taken the time to get your compliance house in order.
Encrypt Those Mobile Devices
CR has given you a “Get Out of Jail Free” card by allowing you to Full Disk Encrypt your portable devices. That way, if they are lost or stolen, you do not have to prove to the government that there was no ePHI on the missing phone or laptop. Android and iPhones/iPads all have built in encryption that only takes minutes to enable. If you have an Exchange email server, it can be configured to not send emails to portable devices if they are not encrypted. For your Windows devices, you will have to purchase a program to do the Full Disk Encryption for each device. While you may not need to encrypt Servers and certain desktop PCs, I would make sure that I had Full Disk Encryption on any device that left the office.
Hank Wagner
757-333-3299 x232
hank.wagner@computernetworksinc.com
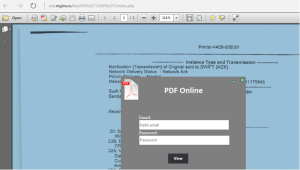
Scam Of The Week: Locked PDF Phishing Attack
Wednesday Jan 4th, the SANS Internet Storm Center warned about an active phishing campaign that has malicious PDF attachments in a new scam to steal email credentials.
The SANS bulletin said that the email has the subject line “Assessment document” and the body contains a single PDF attachment that claims to be locked. A message reads: “PDF Secure File UNLOCK to Access File Content.”
John Bambenek, handler at SANS Internet Storm Center said: “This is an untargeted phishing campaign. They are not going after the most sophisticated users. They are going after Joe Cubicle that may not think twice about entering credentials to unlock a PDF.”